Deeper Connect Wi-Fi Adapter (USB-C)
Applicable to Deeper Connect Pico, Mini
Weight: 8.5 g
Dimensions: 9 × 1.7 × 0.6 cm
Interface: USB Type-C
Package: Weight 37 g
FREE SHIPPING on orders over $99 | Limited Time offer
1-Year limited warranty.
14-day return or exchange guarantee.
Orders are eligible for same-business-day cancellation.
Custom duties are to be paid by the recipient. Duties levied differ across regions.
This product ships to every country (except Mainland China).
*Return,Cancellation and Warranty Policy.
Please keep an accurate personal record of the official order information as our customer service team needs to authenticate the order information in order to provide better after-sales service, including tech support, warranty and/ or replacement.

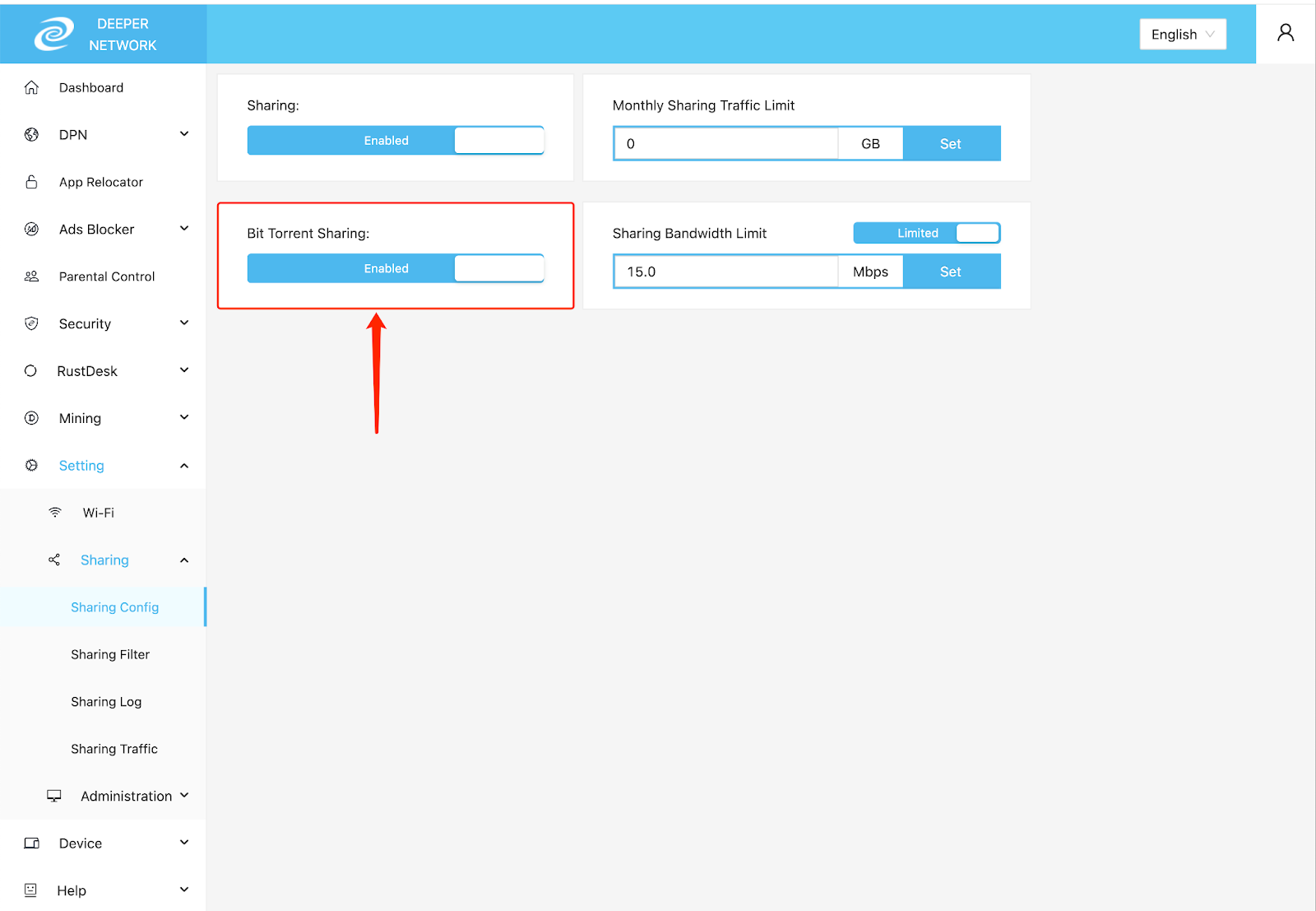
Simultaneous Use

Adapter (USB-C)x1

× 1
Frequently Asked Questions
- DPN
- Troubleshooting
- Product
- Shipping
- Staking
- Charges and Fees
- DPN
- Troubleshooting
- Product
- Shipping
- Staking
- Charges and Fees
-
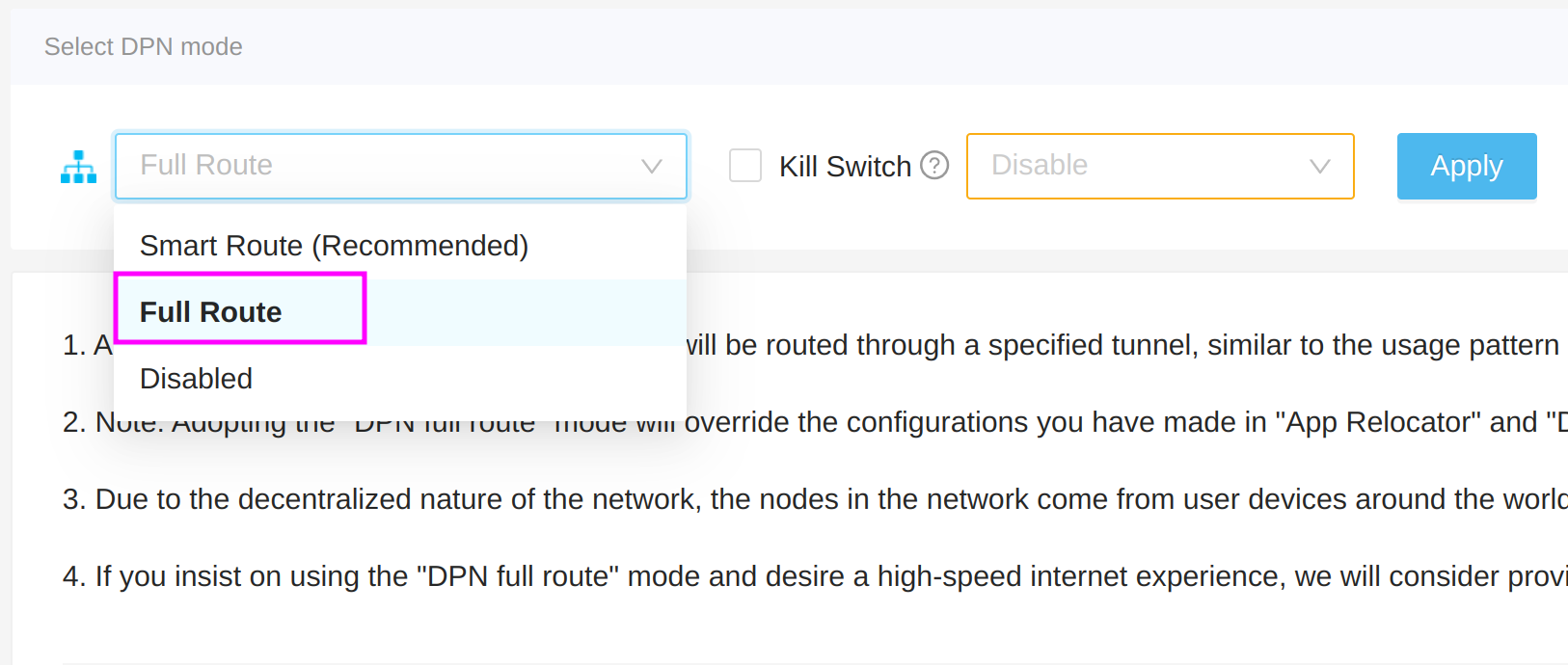
What is DPN and how does it differ from Decentralized VPN?
DPN (Decentralized Private Network) represents a decentralized private network technology and is an abbreviation for DeePer Network. It differs from the traditional decentralized VPNs (Decentralized VPN). While there are many Decentralized VPN projects worldwide, DPN stands out with its unique features. It incorporates enterprise-level network security technology into the Decentralized VPN framework, providing security and privacy for both bandwidth users and providers. This approach ensures that the development of the Deeper Network does not pose significant security risks to bandwidth providers like the TOR Network and other Decentralized VPN projects have, and it avoids the potential for the Deeper Network to evolve in the direction of the dark web. The next question will detail how DPN applies world-leading enterprise-level network security technology to protect the safety of bandwidth providers.
-
Does the DPN technology, based on shared bandwidth, pose cybersecurity risks to bandwidth providers?
Decentralized VPN technology based on shared bandwidth aims to enhance privacy and freedom in network access through bandwidth sharing. However, it may also pose cybersecurity risks to bandwidth providers. For instance, bandwidth requesters might use the technology to download illegal content, launch cyber-attacks, or access harmful websites, and the legal consequences of these activities could mistakenly be attributed to innocent bandwidth providers.
From its inception, the Deeper Network has placed a high emphasis on cybersecurity, striving to address this challenge by incorporating enterprise-level network security technology. To protect the cybersecurity of bandwidth providers, we have implemented the following measures: learn more...
-
What are the notable differences in user experience between DPN and VPN?
1, Cost difference: DPN offers lifetime free usage after purchase, whereas VPN typically requires a monthly fee.
2, Ease of use: DPN deployed using Deeper Connect automatically unlocks regional restrictions for all devices, whereas VPN requires software client installation on each device. Many devices do not support VPN software installation, such as Apple TV. DPN's smart routing feature allows traffic from different applications to automatically switch between countries, eliminating the need for manual node switching required by VPNs.
3, Speed comparison: VPNs provide services through servers, while DPN utilizes the upstream bandwidth of user nodes. Theoretically, VPN speed might be higher than DPN. However, DPN features node aggregation technology, using up to 8 user nodes simultaneously, offering up to 8 times the speed increase. Additionally, DPN's smart routing mode can accelerate streaming media resource access through nearby CDN nodes, reducing the transit delay and buffering common in VPNs.
4, Differences in geo-location unlocking: As more companies start detecting VPN or proxy IP accesses to streaming media (like Netflix), VPN IPs are easily detected. In contrast, DPN uses home IPs of users, reducing the risk of being blocked.
5, Security: DPN integrates enterprise-level network security technology, filtering almost all internet ads and trackers, including some that require paid filtering. DPN is also equipped with advanced intrusion detection technology to identify and block cyber-attacks. Without a central server, user access logs are encrypted and dispersed across global nodes, enhancing privacy protection. In contrast, VPNs store user access logs on central servers, and the service provider may access or even view user data, posing risks of log leakage and selling user data.
-
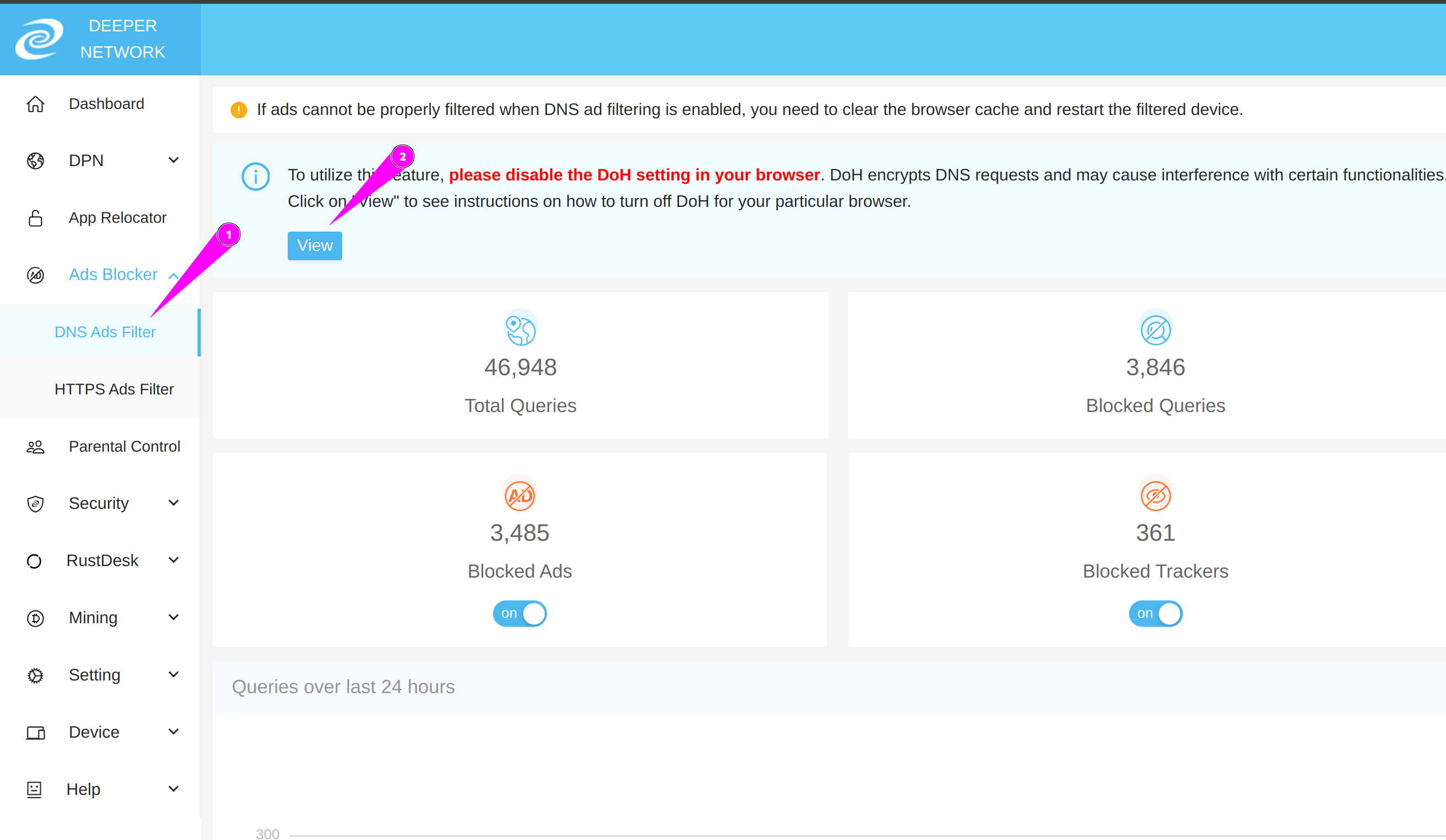
How does DPN's ad-filtering experience differ from Pi-hole?
DPN's ad-filtering experience differs notably from Pi-hole. Pi-hole mainly relies on DNS filtering, controlling access to specific domains, but this method is limited in filtering precision. It cannot filter specific pages or services and is less capable of handling complex, deep-level ads, sometimes leading to the false blocking of normal content. For example, DPN can filter web and mobile YouTube ads and Spotify's built-in ads, while Pi-hole struggles in these areas.
-
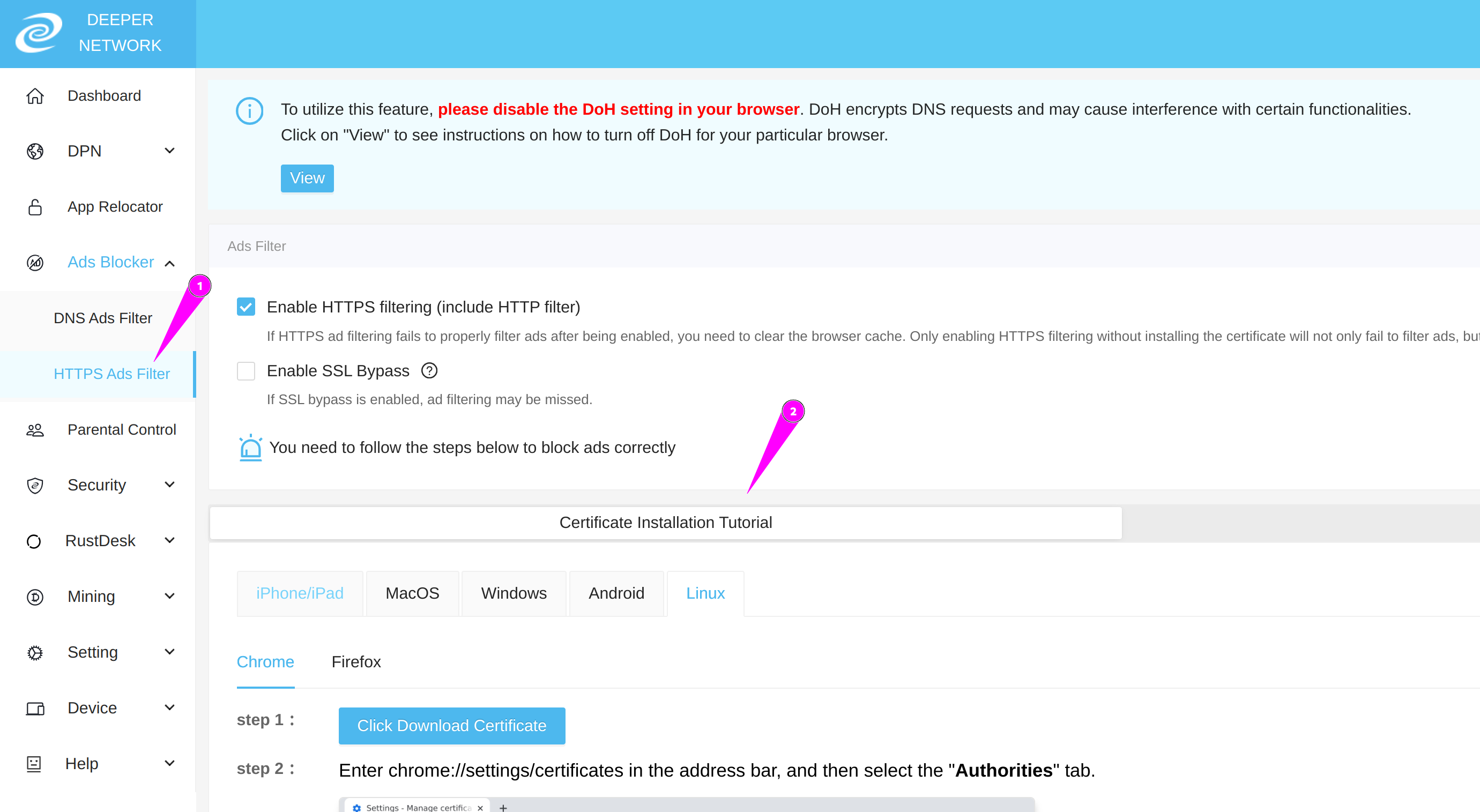
How does DPN's ad-filtering experience differ from browser ad-filtering plugins?
DPN's ad-filtering experience differs from browser plugins in the following ways:
Resistance to countermeasures: Browser plugins are more susceptible to website countermeasures. For instance, sites like YouTube frequently update their recognition codes against browser filtering plugins to prevent ad filtering. DPN's ad filtering, based on underlying traffic filtering, can evade such countermeasures, providing a more stable ad-filtering effect.
Cross-platform capability: Browser plugins usually only run on PC browsers and cannot be used across platforms. In contrast, DPN's ad-filtering functionality can run on multiple platforms including iOS, Windows, Mac OS, Android, TV OS, Linux, etc. This allows DPN to effectively filter ads in popular applications like YouTube and Spotify.
Friendly Reminder: To use DPN's ad-filtering feature, it's necessary to install Deeper Network's SSL root certificate on the terminal device, enabling Deeper Connect to modify underlying traffic.